(Click above for full article with screenshots)
It’s a good idea to keep a thorough record of all jobs you apply for. If you are on unemployment, your state unemployment division will likely require you to keep a record of your job contacts. Even if you aren’t collecting unemployment, it’s still a good idea to keep a detailed record of your applications.
For example, Colorado Unemployment requires you to keep a record of:
• What action you took
• How you applied for the position
• The type of work you were looking for
• The person you contacted, a telephone number,
email address or other reliable contact information
• The outcome of the contact
I keep the information in an Excel spread sheet. Excel is very useful for keeping a list of all my applications. Its search feature makes it especially useful. Years ago, I kept a paper list. I discovered paper lists aren’t handy if I want to search through the companies and jobs I applied to in the past.
Click here for sample spreadsheet
I also added the date, the employer, the website, and a few other fields. If I have an email or phone number, I will specify under employer. If the employer is a recruiting firm, I also include the name of the company they are submitting me to. That way I have a record of the actual company I applied to. That will come in handy if I need to search for companies I applied to. Also, some employers will not accept resumes from recruiting firms if you already applied with them.
Most of the jobs I apply to are on-line. The jobs are listed on job boards or employer websites. Often the job board will contain a job desription with a link to apply for the job. Sometimes the link is to an employer’s website, sometimes the job board will send your resume and cover letter to directly to the employer. I keep a copy of the link under the column “Job Website”.
“How contacted” will contain information such as if I applied via a job board, via a company website, or via email etc. I also specify if I submitted a Resume or both a Resume and Cover letter.
Most jobs will display a message and/or email you that you successfully applied. I keep a copy of the message under the “Confirmation” column.
Some employers will ask where you saw the job posting, so I put that information that under the “Job Board” column.
Most company career sites will ask you to set up an account. I keep the account information under the column “Logon to Employer Site”. I don’t put the actual password I used, instead I put hints to help me remember the login and password.
Job Board Hints
I review the job boards and keep a record of every job I apply for
Here are some of the job boards I visit:
indeed.com
linkedin.com (jobs)
dice.com
monster.com
careerbuilder.com
glassdoor.com (jobs)
ziprecruiter.com
Be aware that some job postings will not direct you to an application page. Some of the links will ask you to provide an email before you can apply. Sometimes, that’s OK. Other times the posting will scrape job listings from other sites and ask you to provide email and other information before directing you to the application page. If you can skip the inquiry, I recommemd you do. Unfortunately it’s not always easy to tell if the link is legitimate or if it’s gathering email so they can send you spam. When in doubt, go directly to the company website and apply through their careers page.
The job boards enable you to limit the number of days back to search. This is useful if you search the boards every day. They’re all a little different, but generally you can limit your search to 1 day back, sometimes 3 days, most will allow you to limit your search to a week back. Look for links such as “advanced search”, “date posted”, “filter”, or similar. I do not see a similar feature on Dice, but Dice does have a “sort by relevance/date” link so you can put the newest postings at the top.
Other Record Keeping and Job Application Hints.
I use an email address dedicated for my job search. This helps me keep my job search emails separate from my regular emails. This makes it less likely I will miss an important job notification. Since I use Microsoft Outlook, I have my Outlook configured to flag incoming job search emails with a special color and musical tone.
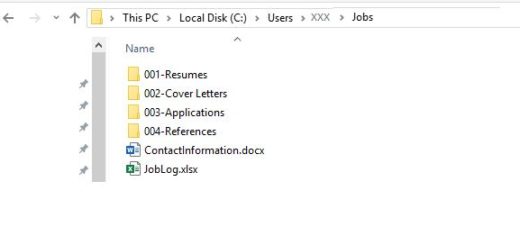
In addition to my log, I keep a “Jobs” folder with several subfolders.
It should be fairly intuitive what most of the folders are used for.
Resumes go in the “001-Resume” folder. I have several different versions of my resume, depending on what I’m applying for.
Cover Letters go in the “002-Cover Letters” folder. Again, I have several different versions of my cover letter, depending on what I’m applying for.
I keep PDF copies reference letters and reference contact information in my “004-References” folder.
My “003-Applications” folders may not be as intuitive at first glance, but it’s a very important folder.
Under “003-Applications, I create an employer sub-folder when I apply for a job. If I apply more than once with an employer, I add the new job info to the folder. Sometimes I may need to create sub-sub folders.
I copy a resume from my 001-Resume folder and I copy a cover letter from my “002-Cover Letter” folder into the employer folder.
I then customize my resume and cover letter to match the job. I may change the order of the items in my resume or cover letter. I may add skills not listed in my original resume to match the job description, and I may change the words and terms in my resume and cover to match the job description. This can be useful for a technical role when …